Why are hospitals still using VPNs?

A Virtual Private Network is a private tunnel from a medical facility’s network firewall to external facility’s network firewall. These are basically holes poked through the main security device designed to prevent outside data from reaching the medical facility’s network. VPNs are complicated to set up and let’s face it: they suck.
VPNs are prone to failure
Every hospital’s network administrator has faced the problem of a failed VPN. Patient care can come to a halt when they are not working. This can happen from one of the following scenarios.
- One of the two facilities in the VPN connection changes their Internet Service Provider (ISP) leading to a new IP address assigned to their external firewall which in turns causes the original IP address used in the configuration of the VPN to fail the connection.
- One of the two facilities changes their network firewall brand, model, or version leading to the other side’s VPN configuration to fail the connection.
- One of the two facilities has a primary network firewall failure and the backup firewall is missing or has an old VPN configuration leading to a failed connection.
- A power spike or other unnatural occurance causes a corrupted configuration file on the primary firewall leading to a failed connection.
No matter the cause the VPN is the 7th item on the network administrator’s list of things to fix and they are probably pulling out their hair at the time it needs to come back up. This leads to delays in patient care due to the timeliness of it coming back up. In the case where a new VPN needs to be established, the network administrator must be on the phone with the external facility’s network administrator to quickly set up and test the new VPN.
When you read “quickly set up” above I bet you thought “how could it be a secure as when it was first established because they are just trying to get data flowing?” You are right to be concerned as many of the VPNs that are re-established in times of bigger failures at the facility are never re-secured later leading to potential holes in the network security at the medical facility.
VPNs are inherently insecure
It takes a lot of work by highly-paid network security personnel to ensure that a VPN is protected. If it is not properly protected the connection can allow any type of data to flow in and out of either facility which can include things such as network files shares, database connections, viruses, and even ransom-ware.
It takes a properly-defined connection architecture with specific limits on the types of data allowed, the IP addresses and subnets allowed to access the connection, and the services allowed over the connection.
This leads to many VPNs being set up quickly and never properly secured because the project needs to be done to meet a patient care need at the medical facility.
And as Edward Snowden recently showed, every Cisco VPN made before 2009 has open holes allowing patient data to be seen from external parties. There are still tens of thousands of facilities using the PIX firewalls from Cisco that have the vulnerability.
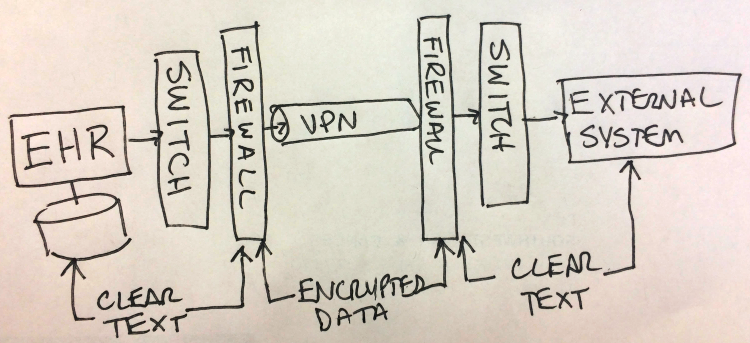
VPNs don’t encrypt data all the way
A connection from one system to another across a VPN is encrypted between the two network firewalls and only between the two firewalls. Here is a drawing from a presentation where it shows where the data is encrypted in a VPN connection. Notice where the failures are in the system.
We do better
Applications can now utilize modern web methodologies and technologies to eliminate VPNs altogether. One such application is made by my company MI7 and is codenamed: Q.
The basics on how the VPN has been eliminated is that network traffic is well-defined to a limited protocol and format, and the data originates from within the medical facility and goes out and only out. It never comes back in from the outside unless drawn down through a well-secured connection using the most secure encryption technologies.
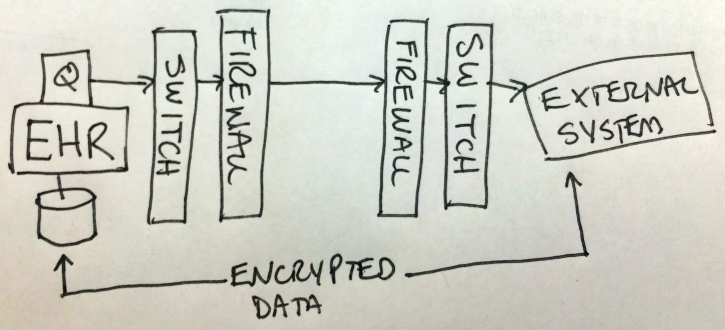
End system-to-end system encryption
The other aspect of VPN-less security is information is encrypted from end system-to-end system ensuring there isn’t a potential for data leakage. Here is the same equipment using the Q software as an example and how it protects the data all the way through the network.
Consider getting rid of VPNs to improve the security of patient data flowing in and out of your medical facility. It will reduce your chances of reporting a data breach.
Please connect with me on LinkedIn if you are interested in talking about transcriptions, HL7, or Q.
If you liked the story please consider recommending it by clicking the heart icon below. You can also follow me on Twitter at @richardbagdonas.
Topics: Healthcare, VPN, Privacy